- Prerequisites: Have your AWS credentials ready, including access key and secret access key, with permissions to access the EKS_READER_ROLE.
- Configuring Playbooks: In the Playbooks dashboard, navigate to Integrations > AWS EKS. Enter your AWS access key ID, secret access key, specify the region of your EKS account and the EKS_READER_ROLE.
- Testing the Integration: Test the integration.
Steps to create a new user:
Step 1: Create a policy (AmazonEKSViewNodesAndWorkloadsPolicy) with this json:
Step 2: Create a role (eks-reader) with the above policy attached
Step 3: Create a another policy (AmazonEKSAssumeEKSReaderPolicy) in your IAM that allows assuming this role with the following json:
Step 4: Create a new user in your IAM with the both the policies created above attached- AmazonEKSAssumeEKSReaderPolicy and AmazonEKSViewNodesAndWorkloadsPolicy.
You don’t need to add any group to the user.Step 5: Once the user is created, create an access key by going to “Security Credentials”.
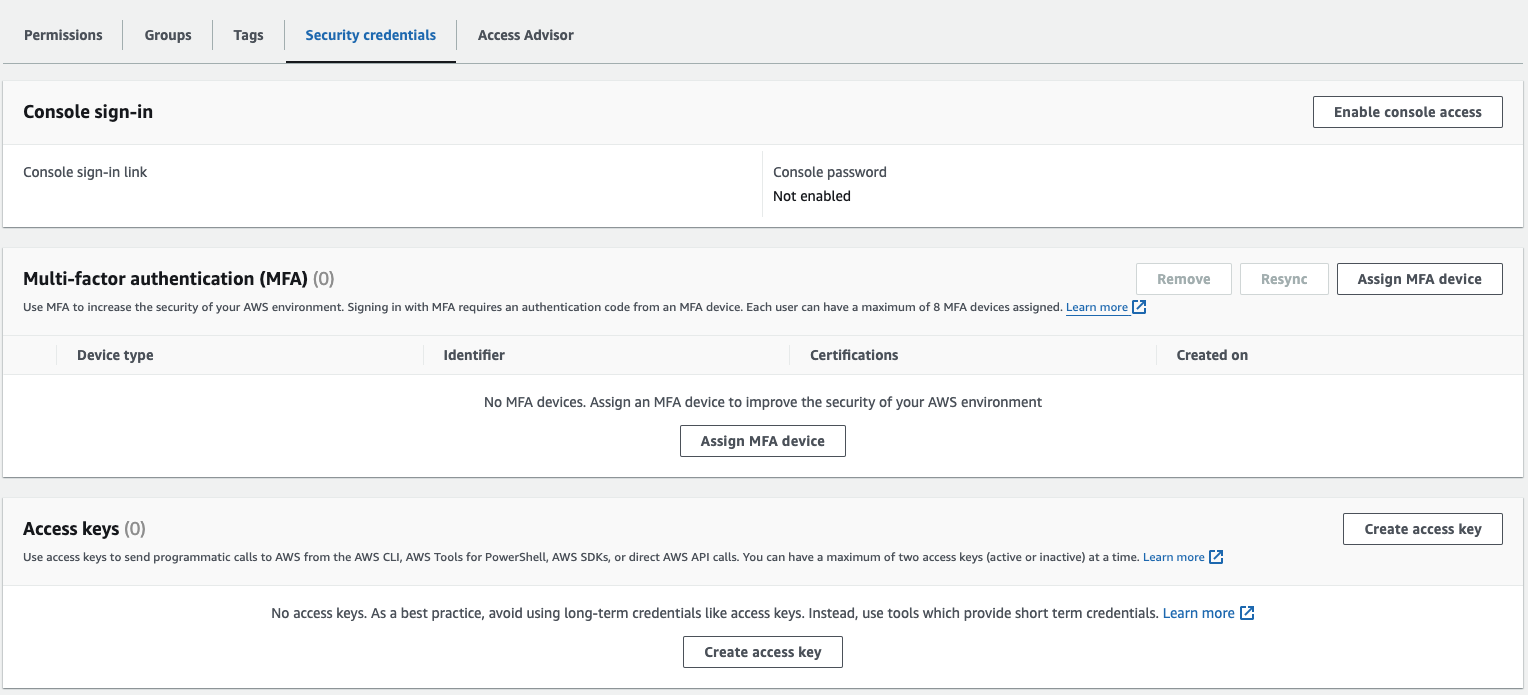
Step 4: Select “Third-party service” while creating the key.
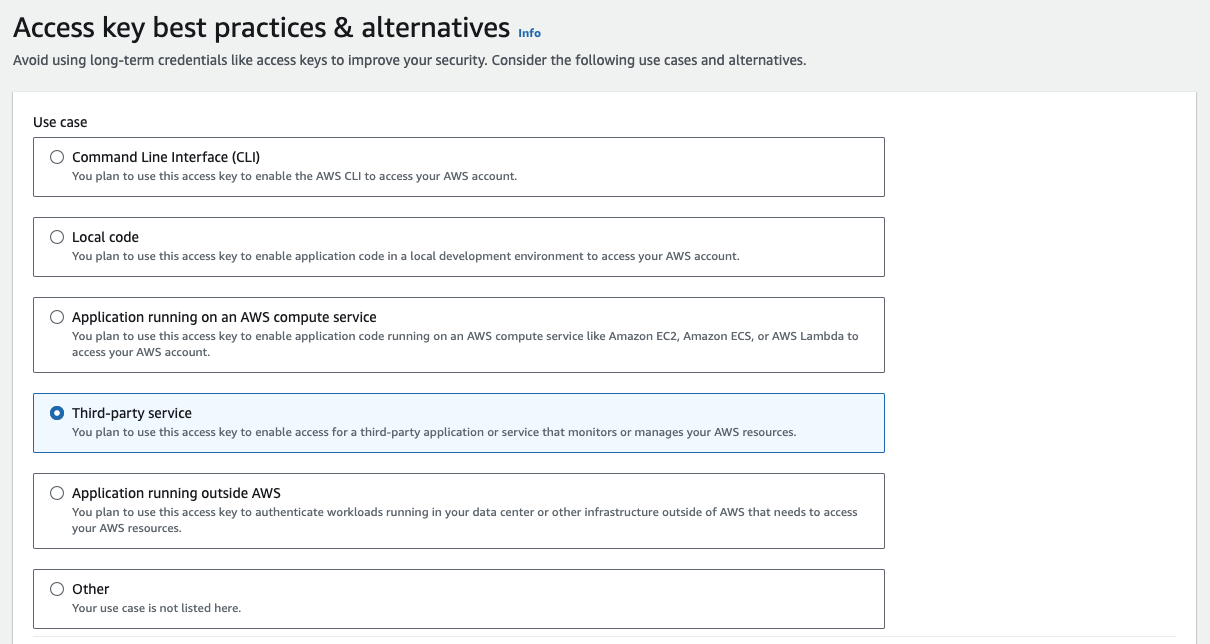
Step 5: Copy paste the access key and secret key in Playbooks Integrations page .
Step 6: Now we will give eks-reader role the permission to query the cluster. We’ll do that by creating a config map, a cluster role and a new role binding.
- kubectl apply -f auth.yaml -n kube-system
- kubectl apply -f role.yaml -n kube-system

