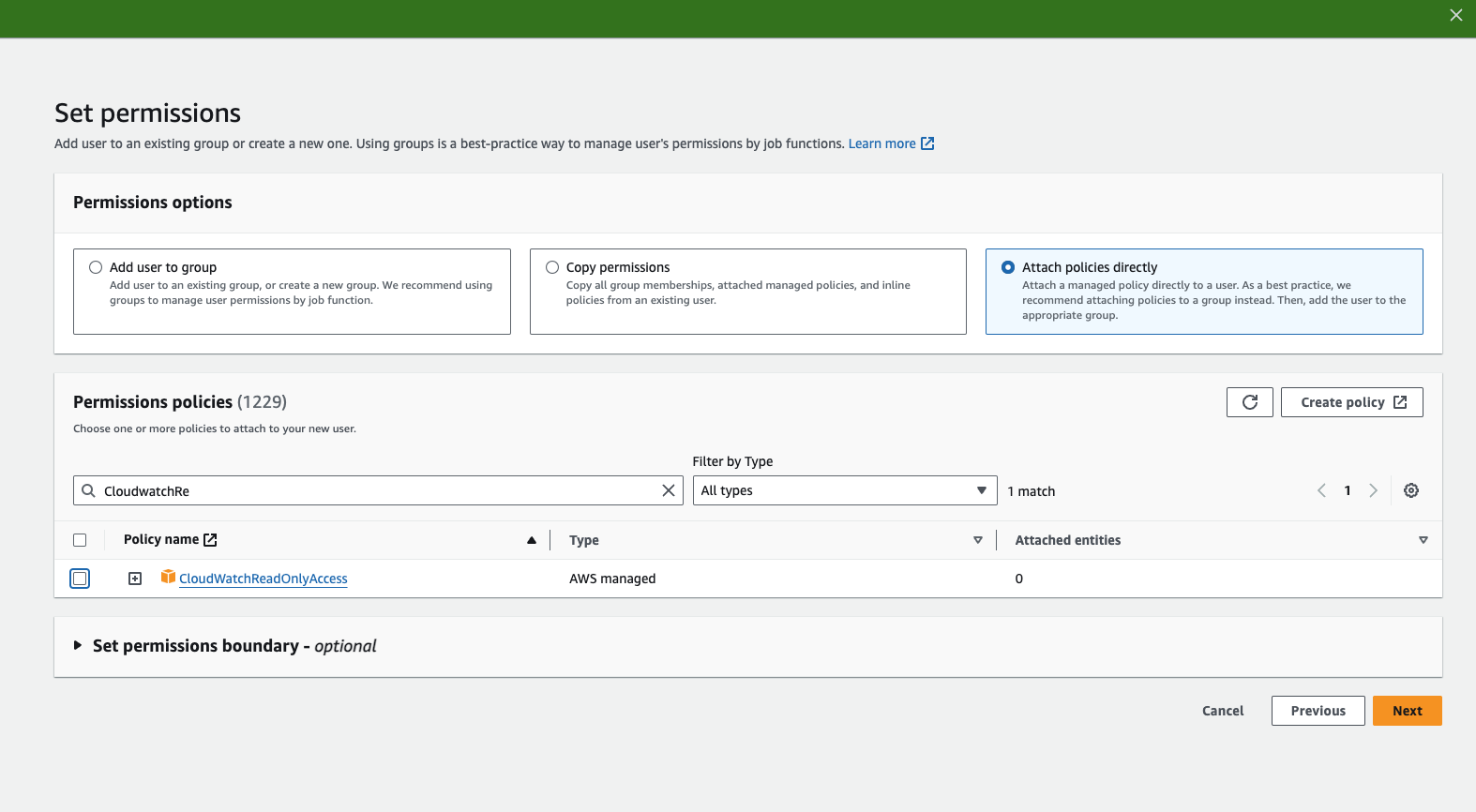
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "InfrastructureInventoryReadOnly",
"Effect": "Allow",
"Action": [
"ec2:Describe*",
"eks:Describe*",
"eks:List*",
"ecs:Describe*",
"ecs:List*",
"elasticloadbalancing:Describe*",
"autoscaling:Describe*",
"rds:Describe*",
"elasticache:Describe*",
"fsx:Describe*",
"kafka:Describe*",
"cloudformation:Describe*",
"cloudformation:Get*",
"cloudformation:List*"
],
"Resource": "*"
},
{
"Sid": "ObservabilityAndUsageReadOnly",
"Effect": "Allow",
"Action": [
"cloudwatch:Get*",
"cloudwatch:List*",
"cloudwatch:Describe*",
"cloudwatch:GenerateQuery",
"logs:Get*",
"logs:List*",
"logs:Describe*",
"logs:FilterLogEvents",
"logs:StartQuery",
"logs:StopQuery",
"logs:StartLiveTail",
"logs:StopLiveTail",
"xray:Get*",
"xray:List*",
"xray:BatchGet*",
"synthetics:Get*",
"synthetics:List*",
"synthetics:Describe*",
"rum:Get*",
"rum:List*",
"rum:BatchGet*",
"sns:Get*",
"sns:List*"
],
"Resource": "*"
},
{
"Sid": "CostExplorerAndBillingReadOnly",
"Effect": "Allow",
"Action": [
"ce:GetCostAndUsage",
"ce:GetCostForecast",
"ce:GetUsageForecast",
"ce:GetReservationUtilization",
"ce:GetReservationCoverage",
"ce:GetSavingsPlansUtilization",
"ce:GetSavingsPlansCoverage",
"ce:ListCostCategoryDefinitions",
"aws-portal:ViewBilling",
"aws-portal:ViewUsage",
"aws-portal:ViewAccount"
],
"Resource": "*"
},
{
"Sid": "CostAllocationTagsReadOnly",
"Effect": "Allow",
"Action": [
"tag:GetResources",
"tag:GetTagKeys",
"tag:GetTagValues"
],
"Resource": "*"
},
{
"Sid": "OptimizationInsightsReadOnly",
"Effect": "Allow",
"Action": [
"compute-optimizer:Get*",
"compute-optimizer:Describe*",
"trustedadvisor:Get*",
"trustedadvisor:Describe*",
"trustedadvisor:List*"
],
"Resource": "*"
},
{
"Sid": "ECRReadOnly",
"Effect": "Allow",
"Action": [
"ecr:GetAuthorizationToken",
"ecr:Describe*",
"ecr:List*",
"ecr:GetDownloadUrlForLayer",
"ecr:BatchGetImage",
"ecr:BatchCheckLayerAvailability"
],
"Resource": "*"
},
{
"Sid": "IAMReadOnly",
"Effect": "Allow",
"Action": [
"iam:Get*",
"iam:List*"
],
"Resource": "*"
},
{
"Sid": "PerformanceInsightsReadOnly",
"Effect": "Allow",
"Action": [
"pi:Get*",
"pi:Describe*",
"pi:List*"
],
"Resource": "*"
},
{
"Sid": "ServiceQuotasReadOnly",
"Effect": "Allow",
"Action": "servicequotas:GetServiceQuota",
"Resource": "*"
},
{
"Sid": "CURAndAthenaReadOnly",
"Effect": "Allow",
"Action": [
"cur:DescribeReportDefinitions",
"athena:Get*",
"athena:List*",
"glue:Get*",
"glue:List*",
"s3:GetObject",
"s3:ListBucket"
],
"Resource": "*"
}
]
}